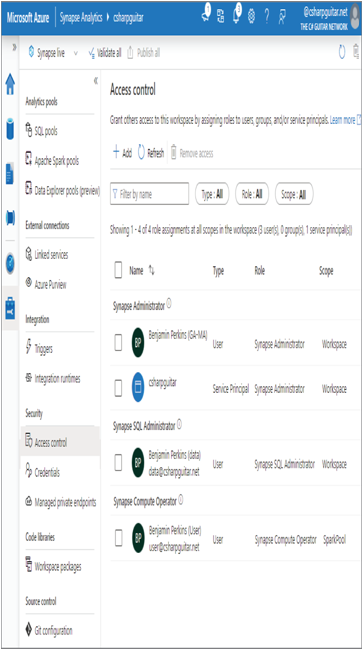
This feature enables you to grant individuals access to either the Azure Synapse Analytics workspace or a single workspace item. When you initially access the Access Control page, you will see something similar to Figure 3.39.
The Access Control page lists the user accounts grouped by Synapse RBAC roles, the type of account, the role, and the scope. Only users who have an account configured into the Azure Active Directory tenant where the Azure Synapse Analytics workspace was provisioned can be granted access. That means user accounts or service principal accounts that meet that requirement will render in the Select User search box, as shown in Figure 3.40. Synapse RBAC roles were introduced in Chapter 1, but you can see some examples such as Synapse Administrator, Synapse SQL Administrator, and Synapse Compute Operator. Each of those roles has a different level of resource permissions, such as reading, writing, or deleting data, making configurations to compute pools, or provisioning new workspace resources. There is a link to all the Synapse roles in Chapter 1.
FIGUER 3.39 The Access Control page in Azure Synapse Analytics
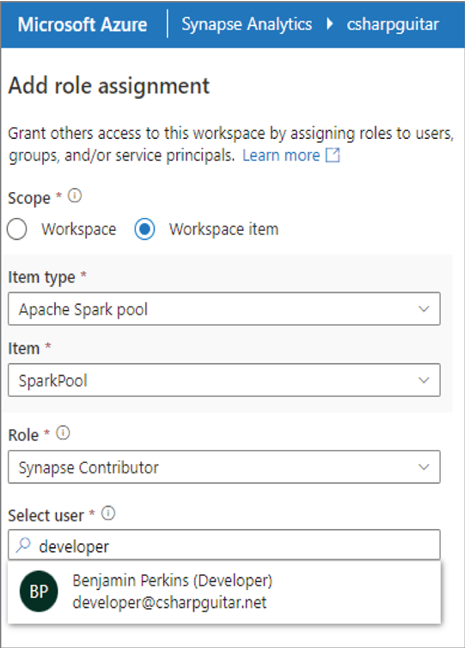
FIGUER 3.40 Adding a role assignment in Azure Synapse Analytics
The different user types can be either a user, a group, or a service principle. Notice that there is a service principle with the same name as the Azure Synapse Analytics workspace. That identity is what is used to grant the workspace access to other Azure resources. For example, in the Azure portal navigate to the ADLS account that you configured when provisioning the Azure Synapse Analytics workspace in Exercise 3.3. Click the Access Control (IAM) link in the navigation menu, and then click the Role Assignments tab. You will see that service principle has been granted access. The service principle is part of the Storage Blob Data Container role. The data in the Scope column, in Synapse Studio, identifies whether the user or service principal account has access to the workspace or a specific item within the workspace. Most of Chapter 8 has to do with security, so if you are interested in that topic now, consider skipping forward (but do come back).
CREDENTIALS
As of this writing, the features available from the Credentials menu item are in preview. This feature has to do with managed identities. As mentioned in the previous section, the Azure Synapse Analytics workspace generates a service principal account, which is used for gaining access to other Azure resources. This feature provides the interface to grant user‐assigned, systems‐assigned managed identities and service principals permission to access the workspace. There is a twist, though. This identity is used in collaboration with resources configured in the Linked Services area. For other resources in the workspace, you can use the capabilities provided via Access Control.
